Key Rotation
Ensures cryptographic keys are set to rotate on a regular schedule
All cryptographic keys should have key rotation enabled. Google will handle the rotation of the encryption key itself, as well as storage of previous keys, so previous data does not need to be re-encrypted before the rotation occurs.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Google Cloud Platform Console.
-
Scroll down the left navigation panel and select the “Cryptographic keys” option under the “Security.”
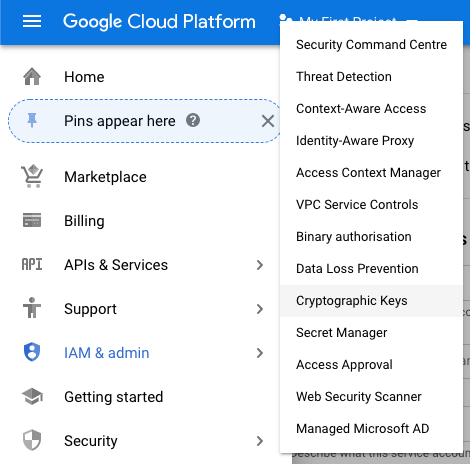
-
On the “Cryptographic keys” page, select the “Name” as a link option to access the key.
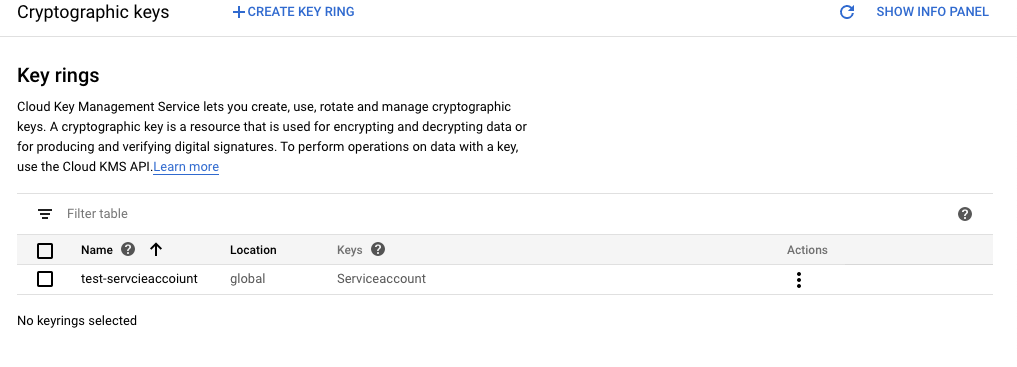
-
On the “Cryptographic keys- Edit” page, check whether the cryptographic keys are set to rotate on a regular schedule or not.
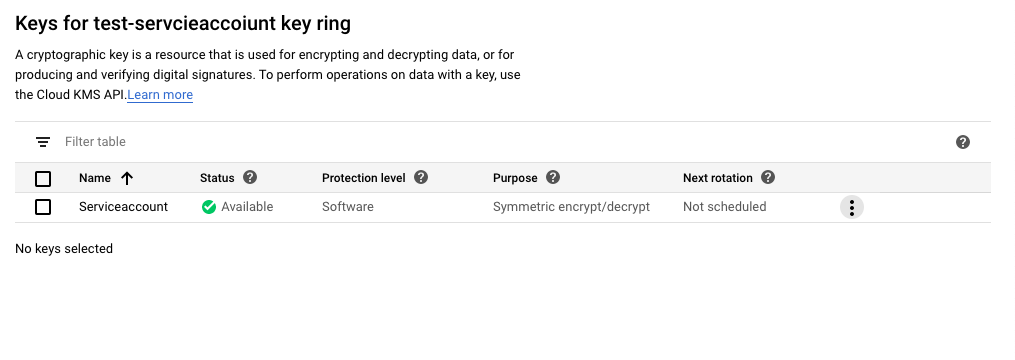
-
Repeat steps number 2 - 4 to check the other cryptographic keys in the account.
-
Navigate to the “Security” on the left navigation panel, select the “Cryptographic keys” option and select the cryptographic key in the question.
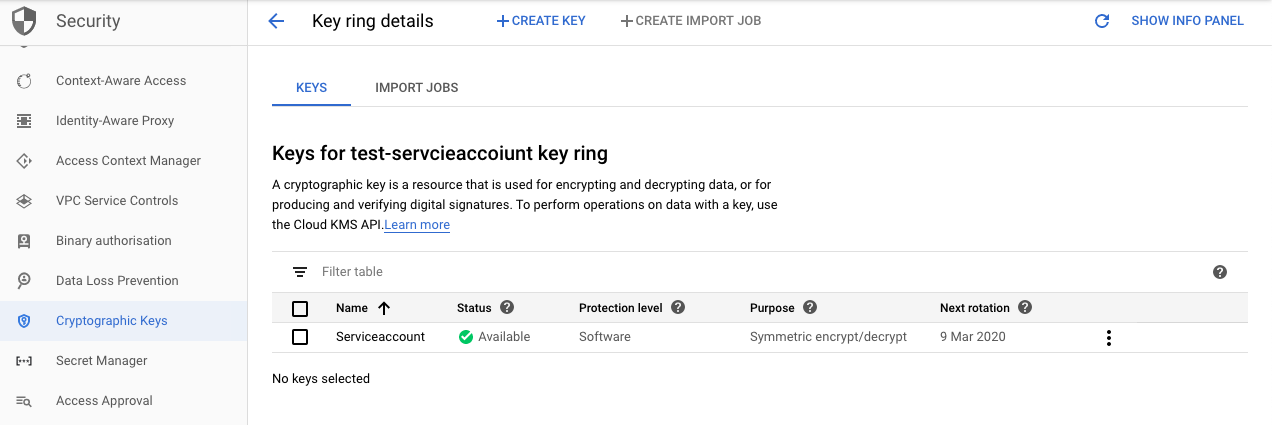
-
Click on the 3 dots at the extreme right to choose the “Edit rotation period” option to change the rotation period to 90 days and click on the “Save” button to make the changes.
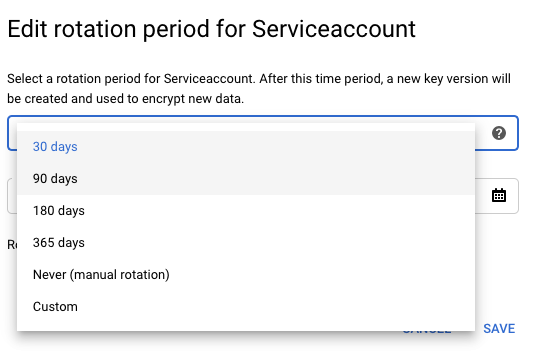
-
Repeat steps number 6 - 7 to ensure that cryptographic keys are set to rotate.