Cloud DNS should use DNSSEC
DNSSEC authenticates DNS responses, preventing MITM attacks and impersonation.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Google Cloud Platform Console.
-
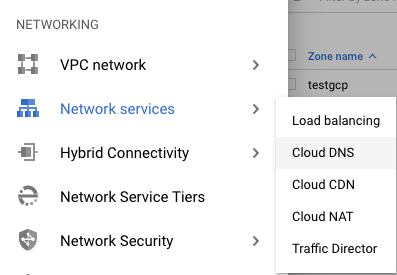
Scroll down the left navigation panel and choose the “Network Services” option under the “NETWORKING” and select the “Cloud DNS.”
-
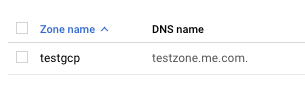
On the “Cloud DNS” page, select the “Zone name” which needs to be checked for the “DNS Security.”
-
On the selected “Zone” check the “DNSSEC” is showing “Off” or “ON”. If it’s turned off then it cannot authenticates all responses to domain name lookups.

-
Repeat steps number 2 - 4 to check other DNS in the account.
-
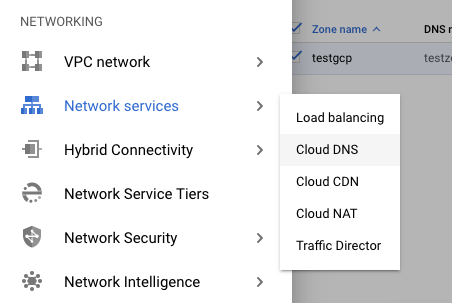
Navigate to the “Load balancing” option under the “Netowrk Services” of the “NETWORKING”, choose the “Cloud DNS” option and select the “DNS”.
-
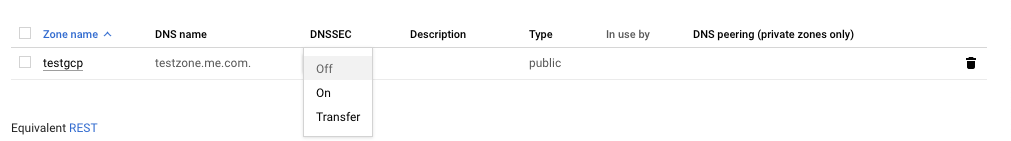
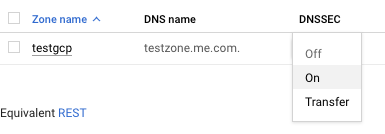
On the “Cloud DNS” place, select the “Zone” and click on the dropdown menu below the “DNSSEC.”
-
On the selected “Cloud DNS”, select the “ON” from the dropdown menu of “DNSSEC.”
-
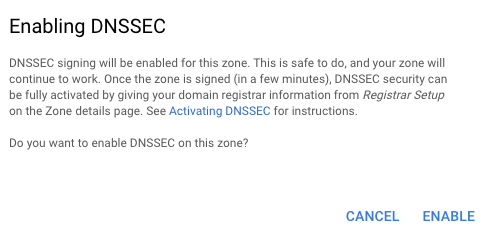
On the “Enabling DNSSEC” tab, click on the “Enable” button to make the changes.
-
Repeat steps number 6 - 9 to ensure “DNSSEC” is enabled for all managed zones in the cloud DNS service.
Enable DNSSEC
|
|
|
|