KMS keys should be rotated at least every 90 days
Keys should be rotated on a regular basis to limit exposure if a given key should become compromised.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Google Cloud Platform Console.
-
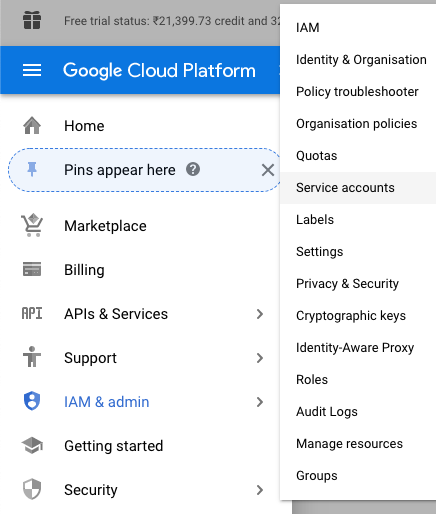
Scroll down the left navigation panel and select the “Service accounts” option under the “IAM & Admin.”
-
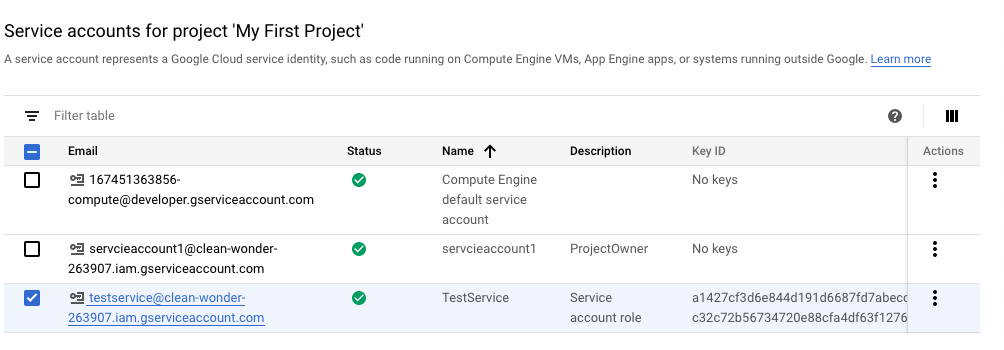
On the “Service accounts” page, select the servcie account with the keys.
-
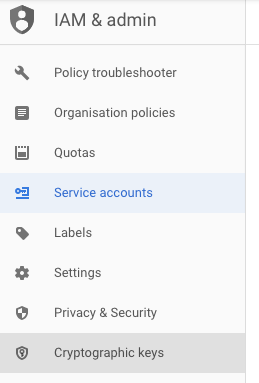
Click on the “Cryptographic keys” on the left navigation panel under the “IAM & admin.”
-
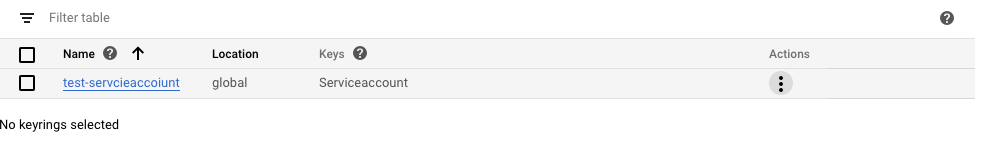
On the “Cryptographic keys” page, click on the “Name” as a link to access the key.
-
On the “Cryptographic keys - Edit” page, check the “Next rotation” date and if it’s more than 90 days then it’s not as per the best practices.
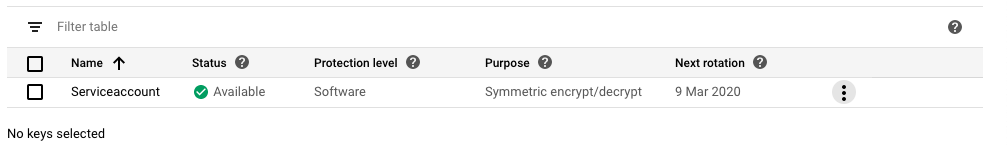
-
Repeat steps number 2 - 6 to verify other keys in the account.
-
Navigate to the “IAM & admin” on the left navigation panel, select the “Cryptographic keys” option and select the cryptographic key in the question.
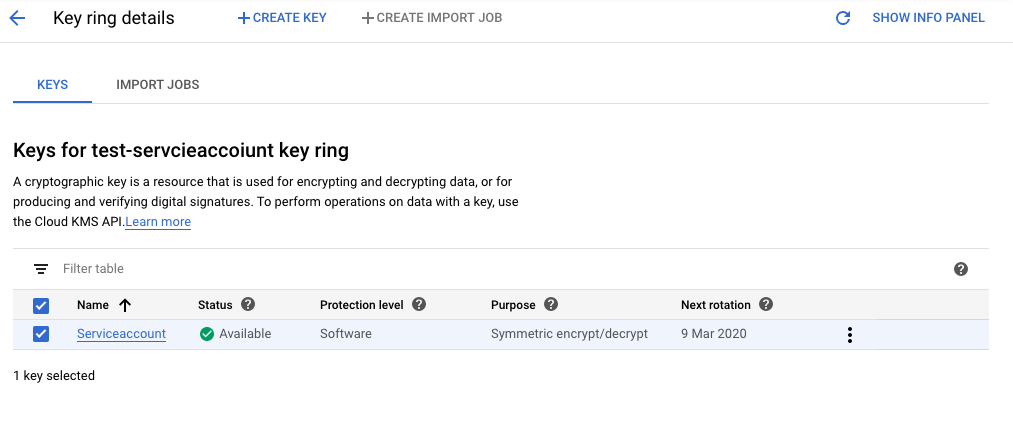
-
Click on the 3 dots at the extreme right to choose the “Edit rotation period” option to change the rotation period to 90 days.
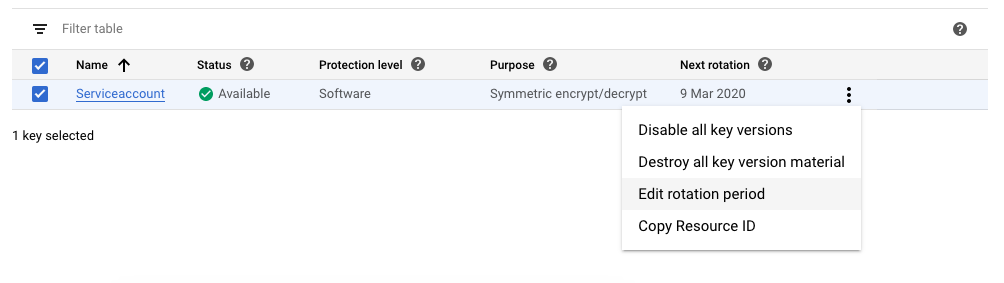
-
On the “Edit rotation period” tab, select the “90 days” option from the dropdown menu and click on the “Save” option to make the changes.
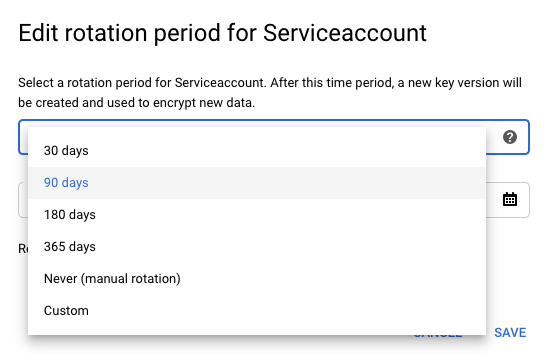
-
Repeat steps number 8 - 10 to rotate service account keys that have not been rotated in over 90 days.
Set key rotation period to 90 days
|
|