Private Access Enabled
Ensures Private Google Access is enabled for all Subnets
Private Google Access allows VM instances on a subnet to reach Google APIs and services without an IP address. This creates a more secure network for the internal communication.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Google Cloud Platform Console.
-
Scroll down the left navigation panel and choose the “Networking” to select the “VPC networks” option under the “VPC network.”
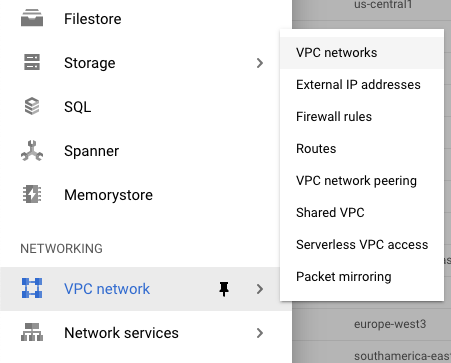
-
On the VPC network page, select the VPC which needs to be verified.
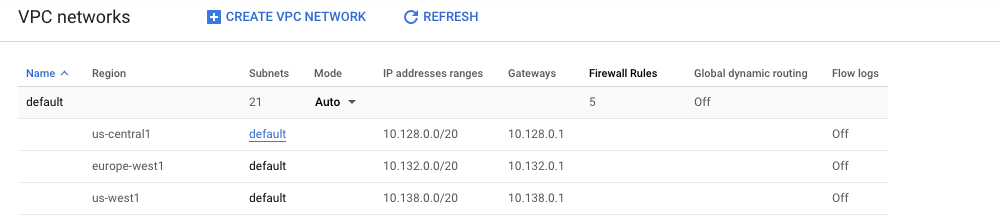
-
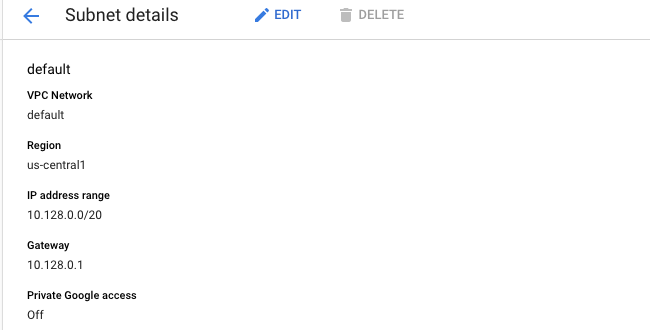
On the “Subnet details” page, scroll down and check the “Private Google access” option. If it’s set to “Off” then the selected VPC don’t have “Google Access” enabled for all the subnets.
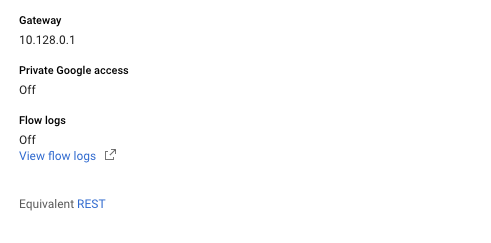
-
Repeat steps number 2 - 4 to verifiy other VPC’s in the account.
-
Navigate to “VPC network” and choose the “VPC networks” option under the “Networking” and select the “VPC network” which needs to enabled “Google Access” for all the subents.
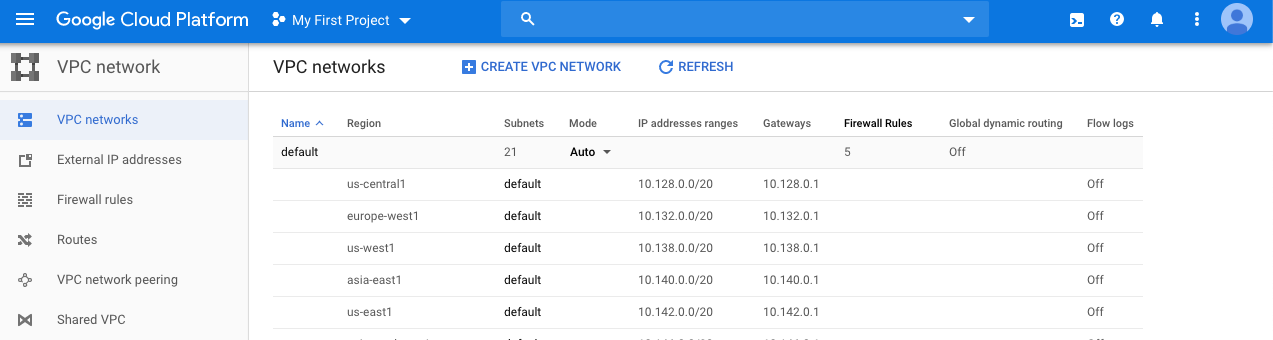
-
On the “Subnet details” page, click on the “Edit” button at the top.
-
On the “Subnet details Edit” page, scroll down the page and click on the “ON” option below the “Private Google access.”

-
Click on the “Save” button at the bottom of the page to make the changes.
-
Repeat steps number 6 - 9 to ensures “Private Google Access” is enabled for all Subnets.