Boot Volume Transit Encryption
Ensures in-transit data encryption is enabled on boot volumes.
Enabling boot volume in-transit data encryption ensures that boot volume data is secured and follows Oracle security best practices.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Oracle Cloud Platform Console.
-
Scroll down the left navigation panel and choose the “Instances” under the “Compute.”
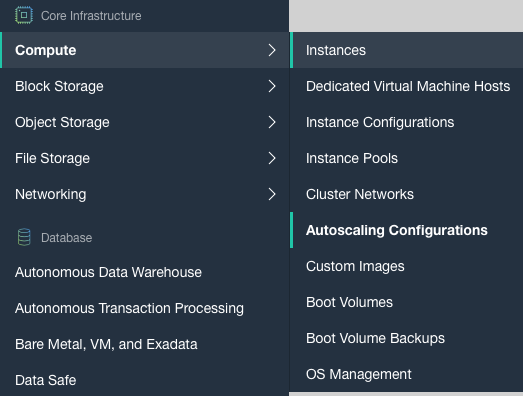
-
On the “Instances” page, scroll down and click on the “Boot Volumes” option at the left.
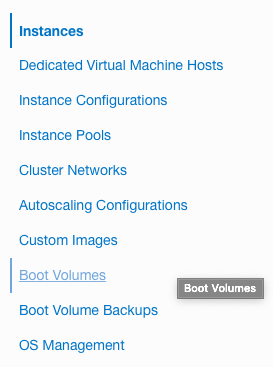
-
On the “Boot Volumes” page, click on the “Name” as a link to access the configuration options.
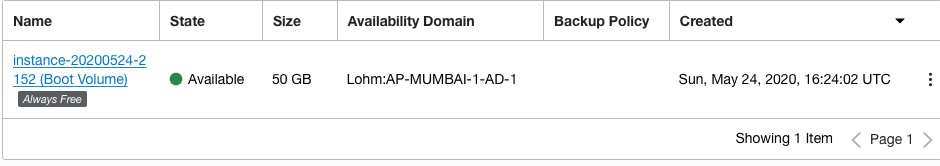
-
On the “Boot Volume Details” page, scroll down and select “Attached Instances” under the “Resources”.
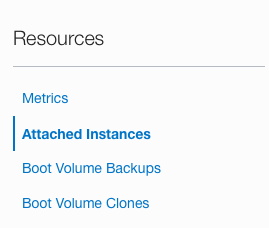
-
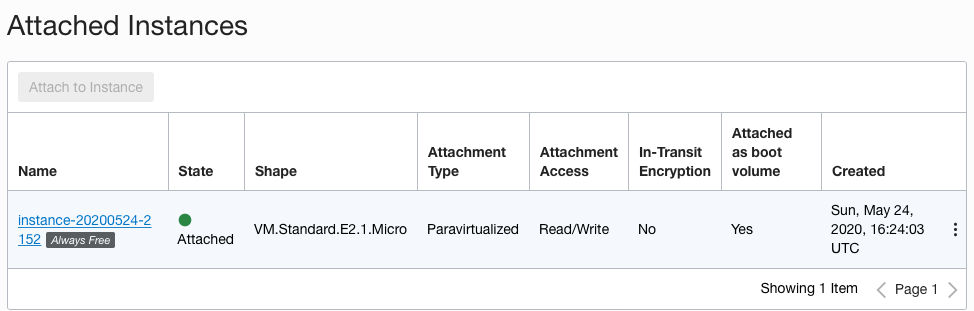
In the “Attached Instances”, check “In-Transit Encryption” is enabled or not.
-
Repeat steps number 2 - 6 to verify other volumes in the account.
-
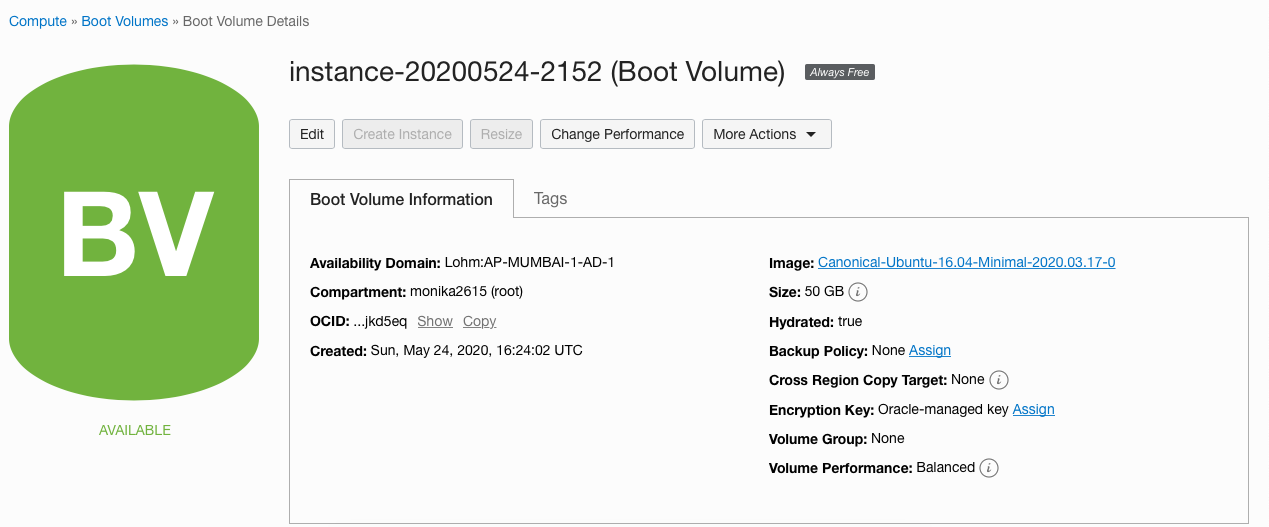
Navigate to “Instances” under the “Compute” and select the “Boot Volumes” option to enable the “Boot Volume Transit Encryption”.
-
On the “Boot Volume” page, scroll down and choose the “Boot Volume Clones” under the “Resources”.
-
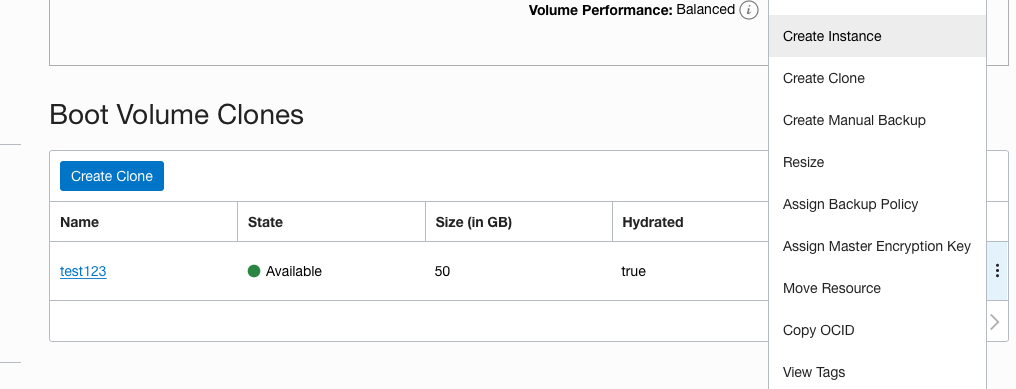
On the “Boot Volume Clones” page, click on the 3dots at the extreme right and choose the “Create Instance” option.
-
On the “Create Compute Instance” page, scroll down and click on the “Show Shape, Network and Storage Options” to expand the services.
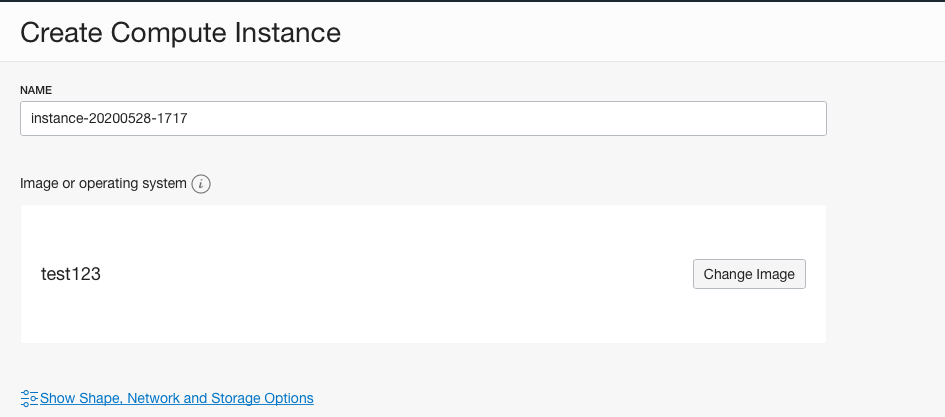
-
On the expand services under “Shape, Network and Storage Options”, scroll down and select the checkbox next to the “USE IN-TRANSIT ENCRYPTION” under the “Boot Volume” and click on the “Create” button to initiate a new Instance.
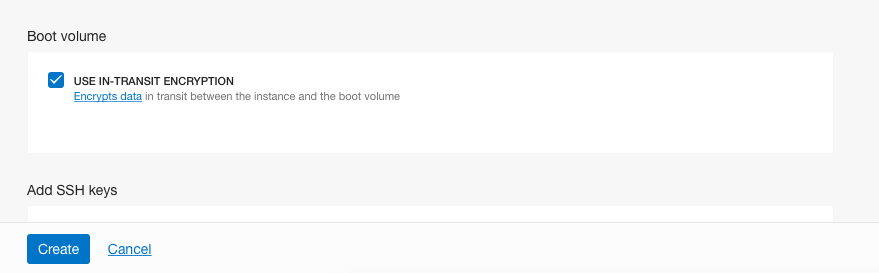
-
Repeat steps number 8 - 12 to enable in-transit data encryption.